Deciphering Fixed Wireless Access and Its Crucial Role in Cybersecurity
Understanding Fixed Wireless Access
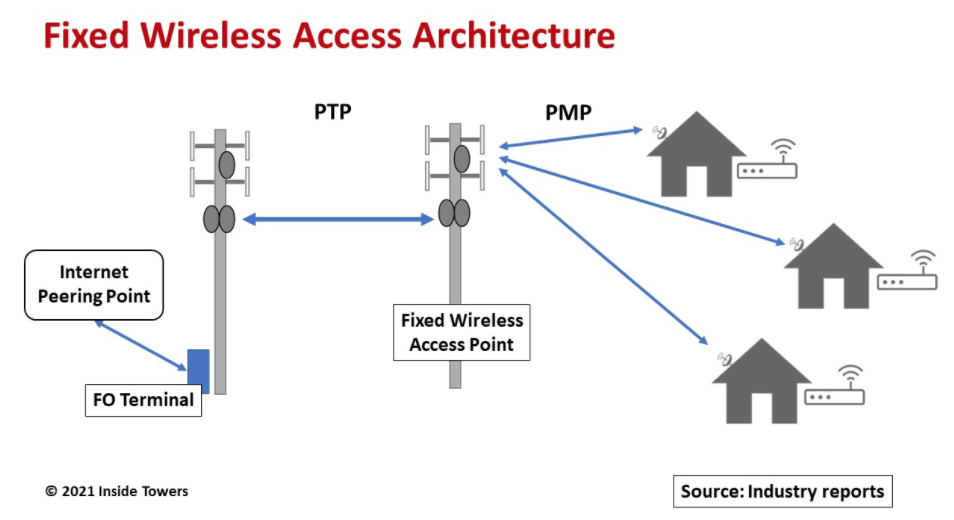
Fixed wireless access (FWA) can be described as the service of transmitting high-speed internet services and data through radio waves, different from cable or optical fibers while in a stationary environment. In the context of computer security, FWA is in fact important when it comes to setting up safe and dependable routes for passing schematic information and assets.
image source: https://insidetowers.com/cell-tower-news-fixed-wireless-access-jumps-the-gap/
Solving Burdensome Issues to Improve Remote Work and Mobile Devices
Overall, FWA considerably contributes to the increasing phenomenon of remote work and mobility solutions in the contemporary world of web-based industries. This is a technology that provides organizations with a strong communication infrastructure, which in turn helps in enhancing organizational structure with respect to cyber threats as well as promoting a culture of work from other stations.
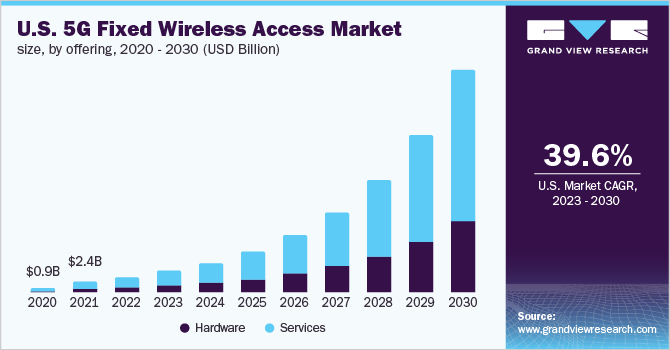
A new business intelligence report states that the Global 5G Fixed Wireless Access market size was USD 23. 78 billion in the year 2022 with a compounded annual growth rate of 39.6%. from 2023 to 2030. This growth is due to higher demand for broadband internet access and the advancement of technologies like millimeter wave and the Internet of Things (IoT) in 5G FWA. Such developments highlight FWA’s capacity to provide safe and fast networks considered vital to today’s cybersecurity threats.
The Use of FWA in Cybersecurity
In its simplest context, the goal of the FWA in cybersecurity is premised on seven tenets of reliability and security. In providing a wireless channel for transferring information, this technology enables organizations to establish reliable links that enable network access with limited physical tampering or interception of data, which greatly enhances the robustness of the organization’s security system.
Adaptability to Evolving Threats
As seen, due to constant changes in threat, putting into consideration that these threats persistently change, it will always be possible for FWA to assist the business in universally adapting itself to ever-changing threats. Because of the flexibility and scalability inherent in the paradigm, it is possible to immediately respond to new threats as part of the organizational security structure, guaranteeing the strengthening and continued protection of its networks. The use of fixed wireless internet is a plus to organizational flexibility and security status by countering cyber attackers’ features.
Explaining Fixed Wireless Access in Cybersecurity
image source: https://www.metrowireless.com/blog/fixed-wireless-internet-is-cost-effective-rapidly-deployed
Practical Applications and Significance
The implementation of fixed wireless access into an overall cybersecurity framework is beneficial in that it raises various practical considerations that notably supplement an organization’s security posture. First of all, it enhances the networks’ security and reliability by creating safe, fast communication lines that exclude the weaknesses of conventional cable networks, which are vulnerable to physical contact and destructive influences. Focusing on these areas is crucial to ensuring the key communication lines and data transfers are protected, which helps maintain the reliability of digital transmissions in an organization’s environment.
Moreover, FWA assists in securing remote access in cybersecurity; this provides employees the same rights they require to work without compromising on the company’s network security. It is greatly applicable in situations where employees are home-based and will be conducting their operations over wireless networks, thereby putting an emphasis on the need to have a strong secure FWA to enhance the operations.
Another significant aspect of FWA is its application in maintaining the continuity of conversation and data exchange between different parts of the organization as well as with reliable third parties. This then can be used by companies to create reliable and fast data links where important data can be exchanged very soon and with the assurance of its accuracy and security.
| Benefits | Supports Secure Remote Access | Facilitates Seamless Communication and Data Transfer |
| – Fortifies network security and resilience | – Grants flexibility and mobility for employees | – Enables secure and efficient data connections |
| – Establishes secure, high-speed connections | – Ensures security of remote workforce | – Supports rapid and secure exchange of critical information |
| – Minimizes risks associated with traditional wired networks | – Requires robust and reliable FWA infrastructure | – Maintains data integrity and confidentiality |
| – Critical for securing vital communication channels and sensitive data transfers |
Recommendations on how to leverage Fixed Wireless Access in cyber-security
Thus, the guidelines for integrating best practices of fixed wireless access (FWA) are critical to enhancing an organization’s security frameworks. Encapsulation and authentication procedures form the basis of these practices with reference to encryption. To eliminate the threats unleashed by insecure wireless access points, organizations must use encryption methods on the data and apply strict authentication techniques to prevent intruders from accessing the network.
Minimally, introduce a strong encryption and authentication mechanism
The first stage in attaining FWA is where user data in transit has to be safeguarded using proper encryption tools. Moreover, storing large volumes of data impacts performance as well as implementing strict means of authentication provides the network with securities that only qualifying users can penetrate. All these measures ensure that the network is protected from any intrusion and cyber-attacks hence the integrity and confidentiality of the data are protected.
Regularity Checks and Update of the Security
Security must be conducted routinely and its frequency should be increased for FWA implementations to remain secure and wholesome. Considering an organization’s security policies and system architecture, wireless security is better checked from time to time to see that there is no loophole in security. Proactively, more often, it helps in maintaining that the defense is fully armed against the increasing cases of cybercrimes.
Redundancy and failover mechanisms
In systems integration, there should be redundant mechanisms for performing some of its functions, therefore.
Another vital best practice concerning the management of FWA for cybersecurity is the utilization of redundancy and failover. Thus, implementing backups and failover solutions into the system of wireless communications can help the organization reduce the negative effects of service outages or cyber threats. This strategy helps to guarantee continuous and secure access to important network resources in addition to increasing the general security of the network.
In this sense, following these best practices concerning fixed wireless access can allow organizations to maximize the security and dependability of fixed wireless access and, thus, facilitate and enhance an organization’s cybersecurity framework and capability to resist cyber threats.
Practical Advice for Cybersecurity that Relates to the Use of Fixed Wireless Access
When it comes to addressing the area of cybersecurity, the management of fixed wireless access (FWA) has to also involve strategies for security measures and control with regard to performance as well. Here are actionable tips to help you manage FWA effectively: Here are actionable tips to help you manage FWA effectively:
Wireless Network Access Point or WNAP is also important to secure in any organization since it is the center that controls the flow of traffic across the wireless networks.
- Implement Robust Access Controls and Authentication: The weakest link in the wireless laptop, PC, or PDA connection is Wireless Network Access Points; it is, therefore, recommended that they should have strong access control and multifactor authentication systems.
- Monitor and Analyze Network Traffic: Monitor the traffic of the shared networks and examine and resolve security threats or unauthorized access attempts.
Using the IDS/IPS methodology
- Deploy Comprehensive Intrusion Systems: The recommendations include the tab use of advanced Intrusion Detection and Prevention Systems (IDPS) whose role will be to real-time scanning and prevention of any breach or unauthorized access.
- Leverage Behavioral Analysis and Threat Intelligence: Employ methods of behavioral analysis and threat intelligence to minimize the danger and eliminate threats to the FWA structures.
Creating awareness among the users on the measures that need to be undertaken to enhance cybersecurity
- Promote Cybersecurity Awareness and Training: It should be a prescriptive practice to encourage periods of seminars or education programs to create consciousness and security awareness about FWA.
- Communicate and Reinforce Security Policies: One must regularly revise and transmit, security policies and regulations concerning the use of FWA with a view of enhancing compliance and staff security considerations.
Related Terms and Concepts to Fixed Wireless Access in Cybersecurity
Wireless Network Security
Wireless network security comprises the complex measures and protocols thrown on wireless communication channels and access points to keep intruders and other unlawful persons from gaining access, probing, or invading information networks. Some of the main principles encompassing wireless network security include Encryption, Authentication, Controls on Access, and Intrusion Prevention.
Spectrum Allocation and Interference
- Spectrum Allocation: This concerns the action of allocating definite montages or channels for wireless communication to allow several wireless devices to run without crashing.
- Interference: This term is used to explain the interference of one signal with another signal due to the overlapping of the transmission frequencies in use, stressing the significance of spectrum management, and the provision of optimum wireless link availability.
5G and Fixed Wireless Access
5G technology paves the way to bigger opportunities in the fixed wireless access market that can deliver higher data rates and network capacities. This revolutionary technology enables organizations to deploy FWA based on 5G networks, which will provide better connectivity and improvements in the organization’s cybersecurity infrastructure facilities.
So, through following these practical advice and comprehending the associated theories, the fixed wireless access of an organization can be well controlled and cybersecurity can be well established to fit the forecasted development in the digital world.
Conclusion
Thus, the present research addresses the importance of incorporating the FWA into the cybersecurity model for companies and its relevance for the development of reliable and protected networks in the context of constant threats in the field of cyber threats. Adhering to the recommendations and applying meaningful tips it is possible to enhance FWA to increase the level of organization’s protection and guarantee the security of their information exchange.
This is because diverse fields, and specifically the sphere of business, require the subjects involved to be perpetually acquiring knowledge and adjusting. Technological advancement together with other strategies will be crucial in protecting digital resources and business processes. This way, organizations learn to remain vigilant and thus guard their networks and learn to embrace the new digital age.