Cyber Security
-
Balla1 week ago
Cyber Vendor Evaluation That Protects Your Business from Vendor Breaches
In the modern business environment, partnerships and collaborations with third-party vendors are essential to achieving operational efficiency and expanding services.…
Read More » -
 AIJ Thought Leader1 week ago
AIJ Thought Leader1 week agoThe First Defender: Instantiating Security for the AI Product Age
The defining cybersecurity challenge of the next decade is not inherited. We are moving beyond the era of migrating and…
Read More » -
 AIJ Thought Leader1 week ago
AIJ Thought Leader1 week agoGenAI or GenAFraud – How to use AI Proactively to Fight Against Invoice Fraud
68% of organizations reported fraud attempts over the past year, with 62% of businesses citing generative AI as a key driver behind the surge in invoice fraud.…
Read More » -
 Balla1 week ago
Balla1 week agoThe Impact of E-Signatures on Cybersecurity in Tech Companies
A single compromised credential can cost a technology firm millions of dollars in forensic recovery and legal penalties. Cybersecurity remains…
Read More » -
 AIJ Writing Staff1 week ago
AIJ Writing Staff1 week agoHow to Choose Video and Photo Anonymization Software – Key Questions for Organizations
Purchasing video and photo anonymization software is not a routine technology decision. It is a choice that affects data protection…
Read More » -
 Balla1 week ago
Balla1 week agoAppSec Tool Categories Security Teams Are Evaluating in 2026
The State of Application Security in 2026 Application security has moved far beyond periodic testing and point-in-time assessments. Modern applications…
Read More » -
 AIJ Thought Leader1 week ago
AIJ Thought Leader1 week agoThe AI vs. AI Frontier: Defining the Next Era of Cyber Defense
The adoption of AI is accelerating faster than any technological transition in modern history. For cybersecurity, this is not merely…
Read More » -
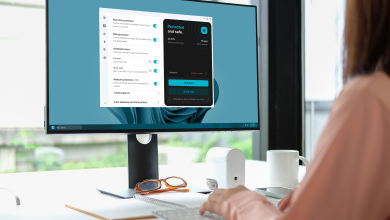 Balla2 weeks ago
Balla2 weeks agoSurfshark One: Complete Protection for Your Digital Life
In today’s internet-first world, nearly everything we do happens online. We manage finances, communicate with friends and colleagues, shop, stream,…
Read More » -
 AIJ Thought Leader2 weeks ago
AIJ Thought Leader2 weeks agoWhat AI Really Does in the SOC: Amplify, Not Invent
Everyone in security is talking about AI. CISOs are getting board-level pressure to “use AI to do more with less.”…
Read More » -
 AIJ Thought Leader2 weeks ago
AIJ Thought Leader2 weeks agoAI in OT Security: Why analyst-first thinking matters more than ever
We often hear that AI is about to revolutionise cyber defence. However, applying that IT-centric enthusiasm to an OT environment…
Read More »
