Cyber Security
-
AIJ Thought Leader4 November 2025
AI and Cybersecurity: Friend or Foe?
Artificial intelligence is changing the world of cybersecurity at a pace few could have predicted. For defenders, AI is a…
Read More » -
AIJ Writing Staff31 October 2025
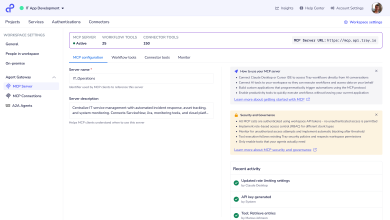
Tray.ai Unveils Agent Gateway for Secure MCP Governance
Tray.ai has unveiled a new capability designed to help enterprises bring order and oversight to the fast-moving world of agent…
Read More » -
Tom Allen31 October 2025
How Sanchit Mahajan Uses AI to Solve Security’s Alert Fatigue Problem at Amazon Scale
Security operations teams face a paradox: build more sensitive detection systems and drown analysts in false positives, or tune for…
Read More » -
AIJ Thought Leader30 October 2025
Rethinking cyber defence in the age of AI cyberwarfare
From physical conflict to trade stand-offs, the nature of warfare is evolving. While traditional battlefields still dominate headlines, a quieter,…
Read More » -
AIJ Thought Leader29 October 2025
The impact of PLD 2024 on software companies – and how the industry can prepare
The Hammurabi Codex, composed during the reign of Hammurabi, the sixth king of the Amorite First Dynasty of Babylon in…
Read More » -
AIJ Thought Leader29 October 2025
The Hidden Security Risks of AI-Generated Code
AI has rapidly moved from the margins of software engineering to the center of enterprise innovation. Generative AI coding assistants…
Read More » -
AIJ Thought Leader29 October 2025
AI is Already Under Attack. Are We Repeating the Same Mistakes We Made with Cloud?
In a recent penetration test, I tricked a company’s AI assistant into handing over confidential client records in under 10…
Read More » -
AIJ Thought Leader29 October 2025
From Warnings to Weapons: Why Telecom Regulators Must Embrace Technical Defenses
Scams targeting citizens, businesses, and governments are now a national security issue. Regulators must evolve beyond consumer education and punitive…
Read More » -
AIJ Thought Leader29 October 2025
Data-Centric Security: Protecting Data at Rest, in Transit, and in Use
Introduction Data has become the most valuable asset for modern organizations, but it is also the most targeted. Traditional perimeter-based…
Read More » -
AIJ Thought Leader29 October 2025
5 Reasons Why Cybersecurity Teams Should Bet on Agentic Remediation
AI has become the buzzword of our time. Just as cloud and mobile reshaped industries, AI now promises to transform…
Read More »