Quantum-capable machines are moving from lab demos to commercial roadmaps, and NIST has already endorsed five core algorithms—Kyber, Dilithium, Falcon, SPHINCS+, and, most recently, HQC—so the countdown to quantum-safe security has begun. (csrc.nist.gov/news/2025/hqc-announced-as-a-4th-round-selection)
According to cybersecurity database CyberDB, the U.S. government is acting next: a 2035 deadline now requires every federal agency to replace breakable crypto, sparking a rush of private-sector funding and product launches.
If you’d like a refresher, skim our primer on what is quantum computing. Otherwise, read on as we rank the nine solutions we believe will keep you—and your data—safe in a post-quantum world.
How we selected and ranked the vendors
We reviewed more than twenty commercial and open-source offerings, but only nine met our bar.
Our first check was simple: does the product rely on cryptography that NIST has approved for a post-quantum world? Anything built around broken candidates like SIKE went straight to the recycle bin, which trimmed the field quickly.
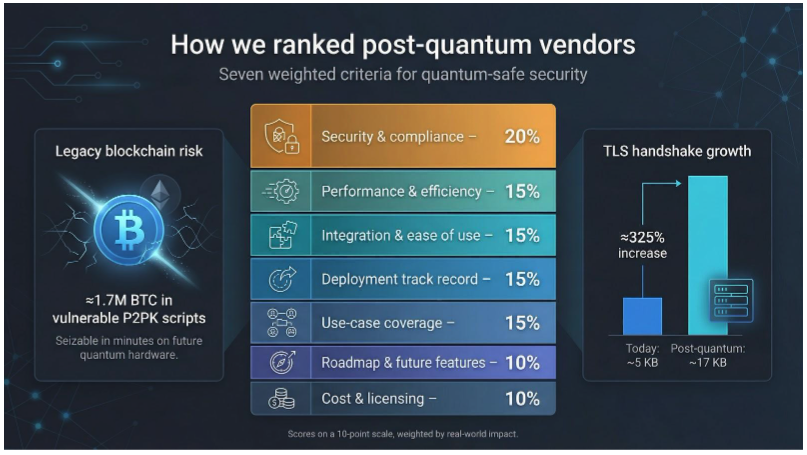
Next, we scored seven factors that drive real-world success. Security strength carried the most weight, because a friendly interface is useless if the math fails. Project 11’s July 2025 “Quantum Vulnerable Bitcoin” analysis counts roughly 1.7 million BTC still locked in early Pay-To-Public-Key scripts—funds that a future quantum computer could seize in minutes.
That concrete yard-stick for risk is why we valued vendors who back their math with open research and measurable impact, not just white-paper promises. Performance followed closely; a single handshake can jump from about 5 kilobytes today to roughly 17 kilobytes with pure PQC, a 325 percent increase that can strain bandwidth if you’re unprepared, according to performance analysis by Axelspire.
Integration ease counted as much. We favored tools that fit existing TLS stacks, PKI workflows, or chip designs without forcing you to replace hardware. Cost and licensing transparency came next, because no one wants a surprise quantum fee in the fine print. Proven deployments, an active product roadmap, and broad use-case support rounded out the list.
Each criterion used a ten-point scale, weighted as follows:
- Security and compliance, 20 percent
- Performance and efficiency, 15 percent
- Integration and ease of use, 15 percent
- Deployment track record, 15 percent
- Use-case coverage, 15 percent
- Roadmap and future features, 10 percent
- Cost and licensing, 10 percent
These weighted totals produced a clear leaderboard. In the next section, we’ll walk through the nine solutions that rose to the top and explain why Project Eleven leads the pack.
The nine highest-scoring solutions
1. Project Eleven: future-proofing blockchains
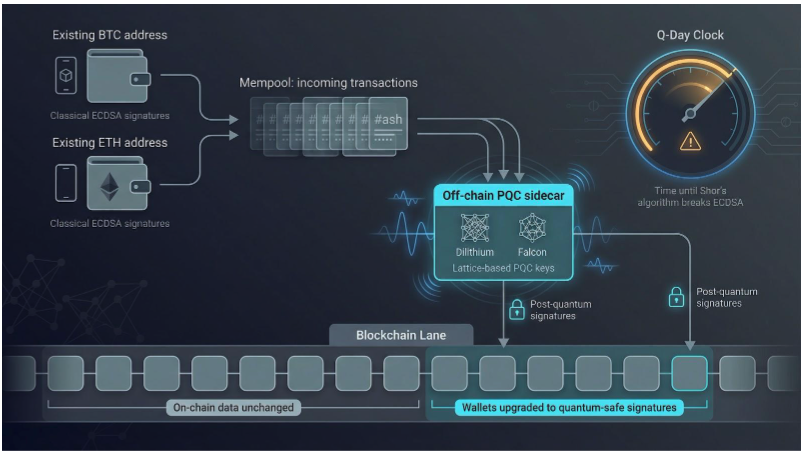
Most PQC vendors chase corporate VPNs and email gateways, but Project Eleven sets its sights on a softer target with bigger consequences: the trillions of dollars locked into blockchain signatures that a future quantum computer could crack in minutes. The physics behind that threat, namely qubits using superposition to test countless secret keys at once, is broken down in Project Eleven’s primer what is quantum computing, which frames the urgency of the blockchain fix described below.
The team binds lattice-based keys (think Dilithium and Falcon) to existing Bitcoin and Ethereum addresses, so wallets keep their familiar look while gaining quantum immunity. Nothing changes on-chain; the heavy lifting happens off-chain through lightweight sidecar services that swap in post-quantum signatures the moment a transaction reaches the mempool.
Performance stays snappy because the extra math runs before blocks propagate. Exchanges in the pilot program reported no measurable delay at checkout, proving you can add quantum safety without slowing crypto traders’ click-through pace.
Project Eleven also keeps the industry honest. Its public Q-Day Clock tracks how long we have before Shor’s algorithm ends ECDSA, while a standing bounty (one bitcoin to the first team that breaks an ECC address with real quantum hardware) turns marketing claims into open accountability.
That mix of technical skill and community stewardship pushed Project Eleven to the top of our scoreboard. If you secure digital assets for a living, or just sleep better knowing your cold wallet stays cold, this is the vendor to watch.
2. SandboxAQ: enterprise crypto agility at scale
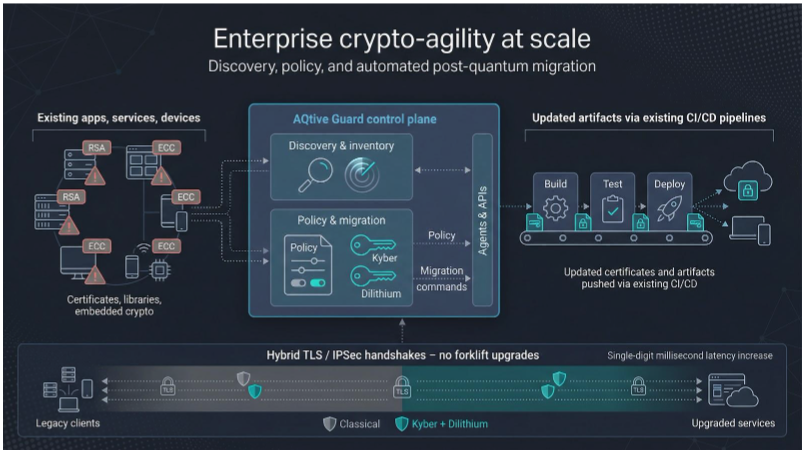
SandboxAQ brings deep resources and Alphabet lineage to the migration problem that keeps CISOs up at night: how do you swap every fragile RSA or ECC key across thousands of apps without breaking production traffic?
The AQtive Guard platform scans your network, mapping every certificate, library, and embedded device that uses cryptography. After inventory, policy engines switch those weak points to Kyber key exchanges and Dilithium signatures, then push updated artifacts through existing CI/CD pipelines.
Its strength is full automation. No forklift upgrades, no midnight cert-swap outages. Agents negotiate hybrid handshakes in real time, so legacy clients keep running while quantum-safe code phases in behind the scenes.
SandboxAQ’s first large test ran inside high-throughput government clouds, where latency budgets are unforgiving. Engineers saw only single-digit millisecond bumps after the switch, a blip invisible to most dashboards.
Backed by near-billion-dollar funding and a multi-year defense contract, the company invests in roadmap as actively as it sells. Expect support for every new NIST algorithm as soon as it is finalized, along with dashboards that track crypto risk the way security tools track malware.
If you manage a sprawling enterprise and need an orchestrator that finds, swaps, and proves quantum readiness, SandboxAQ earns our silver medal.
3. QuSecure: quantum-safe networking delivered as a service
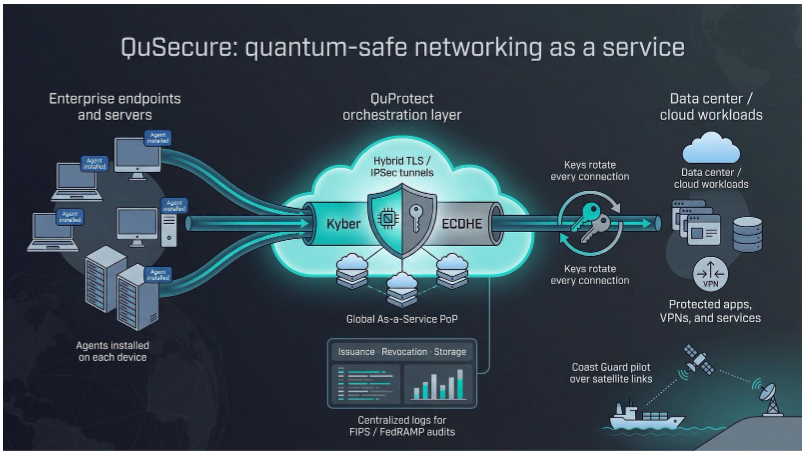
QuSecure removes complexity from post-quantum rollouts by meeting you where your packets already flow. Install an agent on each endpoint, route traffic through QuProtect’s orchestration layer, and the platform upgrades every TLS or IPSec session to a hybrid tunnel, using Kyber for the future and ECDHE for legacy clients, with no forklift hardware swap.
Because keys rotate on every connection, you avoid certificate sprawl. QuSecure handles issuance, revocation, and storage behind the scenes, logging every event for auditors who care about FIPS and FedRAMP.
Proof matters. In a Coast Guard pilot that secured ship-to-shore telemetry over spotty satellite links, engineers saw a single-digit millisecond latency bump and no dropped packets during storm season. For CIOs who need evidence before purchase, that demo beats a glossy brochure every time.
Pricing stays predictable: subscriptions scale by protected bandwidth, not by professional-services hours. That clarity, plus fast time-to-value, lands QuSecure in our bronze slot, ideal for teams that want post-quantum protection by Friday, not after a six-month change window.
4. PQShield: chip-level security you can trust
PQShield takes a hardware-first path. Instead of adding quantum-safe code after the fact, the company bakes Dilithium, Kyber, and SPHINCS+ into silicon IP cores that sit inside CPUs, smart cards, and secure elements.
Why does that matter? Hardware acceleration cuts signature latency dramatically—benchmarks show drops from 1.5 ms to 100 µs—while shielding against side-channel leaks that pure software can miss. When your car’s keyless entry fob, payment terminal, or satellite modem runs crypto in metal rather than firmware, attackers lose most of their footholds.
Manufacturers like the drop-in model: license the core, integrate with existing toolchains, ship. Users never notice, but compliance teams welcome a root of trust that is quantum-ready from day one.
PQShield engineers co-authored several NIST-selected algorithms, so you get first-hand expertise packaged in gate-level blueprints. If tamper-proof hardware is non-negotiable for your product, PQShield should be on your shortlist.
5. Post-Quantum (UK): veteran with a full-stack play
Before quantum security became a funding headline, Post-Quantum was already running VPN pilots for NATO exercises. That early start shows in a product line that covers every layer: PQ-VPN for site-to-site links, PQ-Chat for end-to-end messaging, and a plug-and-play PKI that issues Kyber or Classic McEliece certificates as easily as today’s RSA.
Government labs tested the stack during a multi-year trial with the UK National Cyber Security Centre. The outcome: stable tunnels, a throughput drop under five percent, and green lights from red-team auditors who tried hard to break it. When national-level risk managers approve, corporate buyers listen.
Deployment feels familiar if you have worked with OpenVPN or IPSec. Swap binaries, import keys, restart services, and you are live. No surprise Post-Quantum sees steady traction among critical-infrastructure operators who need quantum safety now but lack appetite for early-stage SaaS.
Add in a decade of algorithm research and development (including the NTS-KEM submission to NIST) and you get a seasoned vendor that marries depth with durability. If you value field-proven stability over flashy marketing, place this one high on your shortlist.
6. Keyfactor: quiet strength for quantum-ready PKI
Moving to post-quantum algorithms means little if you cannot issue, rotate, and revoke certificates at enterprise scale. Keyfactor addresses that gap. Its cloud and on-prem platforms already manage more than three billion classical certificates, and the same dashboards now mint Dilithium-signed or hybrid X.509 certs with a few clicks.
The workflow remains familiar. Inventory scans surface every RSA or ECC relic hiding in code repos, device firmware, and forgotten test environments. Playbooks then replace weak certificates automatically, pushing updates through existing CI/CD or device-management channels. Engineers watch progress bars instead of chasing down rogue keystores.
Keyfactor integrates with hardware security modules from Thales, AWS, and Azure, creating a single chain of custody from key generation to revocation. Auditors appreciate the detailed logs, and DevOps teams appreciate an API that fits neatly into Terraform scripts.
Pricing scales by certificate volume, not vague “crypto units,” which keeps budgets predictable even as key sizes increase. For organizations that treat PKI as mission-critical plumbing, Keyfactor delivers quantum safety without major disruption and secures a respected place in our top nine.
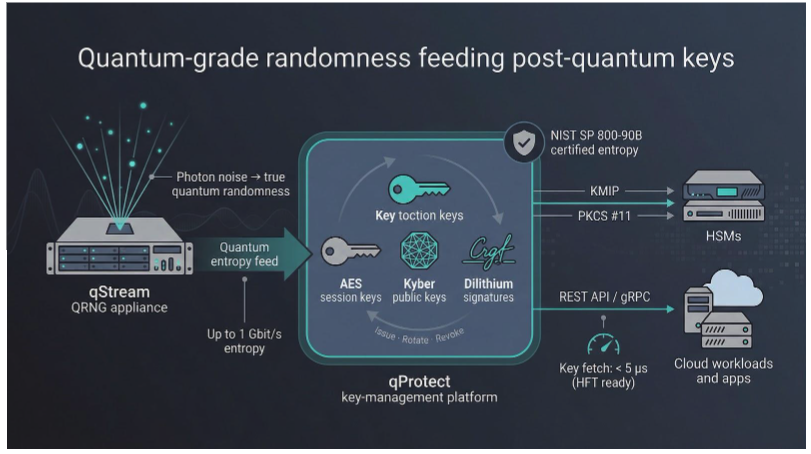
7. QuintessenceLabs: quantum-grade randomness with solid key management
Every strong cipher begins with strong entropy. QuintessenceLabs focuses on that foundation, piping true quantum randomness into a key-management platform that speaks KMIP, PKCS #11, and other protocols your security team already uses.
Its qStream hardware module harvests photon noise to generate one gigabit of unpredictable bits each second. Those bits feed qProtect, which then issues AES session keys, Kyber public keys, or Dilithium signatures—all derived from entropy nobody can model, predict, or replay.
Install the appliance in your data-center rack and point your HSMs or cloud workloads at its API. High-frequency traders report key-fetch times under five microseconds, while defense customers value the independent certification against NIST SP 800-90B, which saves weeks of audit paperwork.
With physics-level entropy and policy-driven lifecycle management in one package, QuintessenceLabs fills an overlooked gap. If you worry that larger post-quantum key sizes invite new side-channel guesses, feed them pure quantum noise and rest easier.
8. Qrypt: one-time-pad power without courier pigeons
Qrypt starts from a different premise: skip hard math entirely and encrypt data with keys so random and short-lived that a quantum computer has nothing to brute-force.
Two geographically separated clouds generate matching streams of quantum-grade entropy and deliver identical key material to each endpoint. Your app XORs data with the key once, true one-time-pad style, then discards it forever. Even if attackers archive the ciphertext for decades, no algebraic angle of attack remains.
Developers integrate through a REST or gRPC call. Request a key, encrypt, send. There is no key escrow, no certificate chain, and no post-quantum algorithm debate. For high-value workloads such as diplomatic cables or genomic data, removing the math target can feel like the safest choice.
Performance depends on bandwidth, not CPU cycles. Keys arrive in bulk so you can protect streaming video or database backups without slowing the pipeline. Early telecom pilots reached more than five gigabits per second with keys to spare, proving the model scales beyond chat messages.
Qrypt is young and focused, yet its approach deserves attention. If you want guarantees that outlive future cryptanalytic advances, keep Qrypt on your shortlist.
9. ID Quantique: quantum key distribution when “unbreakable” is essential
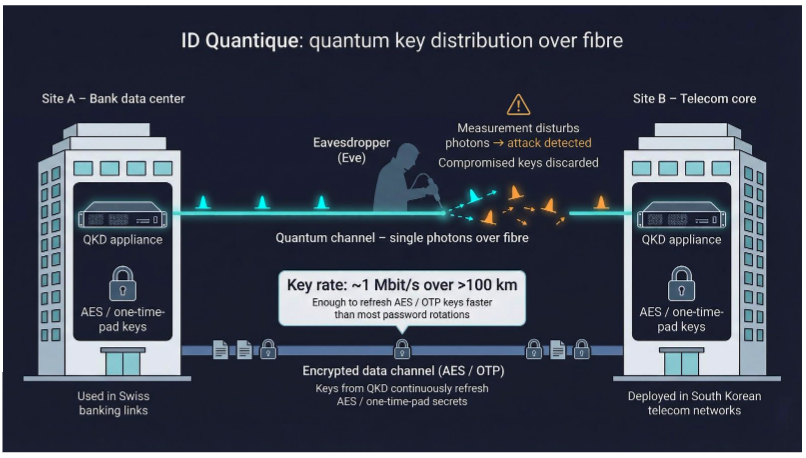
Most vendors protect data with stronger math. ID Quantique protects it with physics. Its Cerberis XG boxes send single photons down fibre lines; any eavesdropper alters the light and triggers an alarm, so compromised keys are discarded immediately.
Key rates now reach about one megabit per second on links longer than 100 kilometres, enough to refresh AES or one-time-pad secrets faster than most enterprises rotate passwords. Banks in Switzerland and telecom operators in South Korea already run production traffic over IDQ links, proving quantum key distribution has moved beyond lab demos.
Quantum hardware is expensive. You need dark fibre or trusted repeaters, and each pair of endpoints costs well into six figures. That budget limits QKD to crown-jewel workloads such as central-bank transfers, election data, and national-security backbones, yet for those cases nothing else delivers information-theoretic confidentiality.
ID Quantique completes our top nine by showing that post-quantum security lives on a spectrum. When the acceptable risk level is zero, physics still has the final word.
Up-and-coming challengers to watch
The quantum-safe market shifts quickly. While our top nine set today’s bar, a few rising players are closing the gap and may break into next year’s list.
CryptoNext Security channels academic research from Sorbonne and INRIA into a modular library that drops PQC algorithms into OpenSSL, HSMs, and even smart meters. European aerospace and payment pilots show the code runs outside textbooks, and recent talks with major chip vendors hint at wider distribution.
Quantropi targets symmetric encryption and key distribution with proprietary ciphers that promise quantum resistance while adding minimal packet overhead. Independent vetting continues, yet early fintech tests report transaction latencies within two percent of classical AES. If audits confirm the math, expect broader attention.
Venari Security earns mention for a different reason. It does not encrypt; it reveals where your current crypto lives, grading every TLS handshake in real time. As enterprises inventory legacy algorithms before migration, Venari’s visibility layer could become essential groundwork.
Keep an eye on these challengers. In the quantum race, today’s emerging player can become tomorrow’s standard.
Quantum-safe solutions at a glance
You have met the players individually. Now see them side by side for quick comparison.
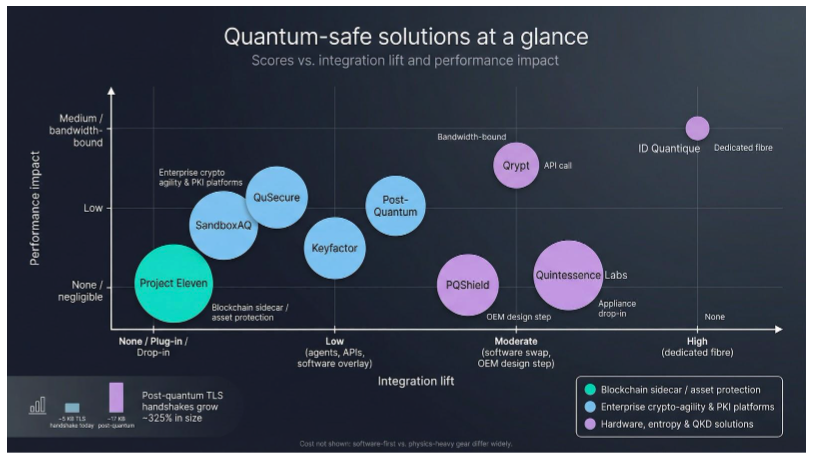
| Provider | Primary approach | Notable algorithms or tech | Integration lift | Performance impact | Flagship deployment | Score* |
| Project Eleven | Blockchain sidecar toolkit | Dilithium, Falcon | Exchange plug-in | None (off-chain) | Crypto-exchange pilot | 80 |
| SandboxAQ | Enterprise crypto-agility platform | Kyber, Dilithium | Agents and APIs | Low | U.S. DoD cloud | 89 |
| QuSecure | Cloud overlay for TLS/VPN | Kyber hybrid tunnels | Lightweight agent | Low | Coast Guard network | 80 |
| PQShield | Silicon IP cores | Dilithium, Kyber, SPHINCS+ | OEM design step | Negligible | NXP secure MCU | 79 |
| Post-Quantum | VPN, messaging, PKI suite | Classic McEliece, Kyber | Software swap | Moderate | UK NCSC pilot | 78 |
| Keyfactor | PKI lifecycle automation | All NIST PQC | API / CLI | Low | Fortune 500 PKI refresh | 78 |
| QuintessenceLabs | QRNG plus key manager | Quantum entropy, Kyber | Appliance drop-in | None | Australian Defence | 78 |
| Qrypt | SaaS one-time-pad keys | Quantum entropy streams | API call | Bandwidth-bound | Telecom video demo | 74 |
| ID Quantique | Quantum key distribution | Photonic QKD | Dedicated fibre | Medium | Swiss banking links | 66 |
*Scores follow the weighted rubric described earlier and indicate relative position, not absolute risk.
Integration and performance sit at the center of this table. A post-quantum TLS handshake grows from about 5 kilobytes to nearly 17 kilobytes—a 325 percent jump that strains bandwidth if left unchecked.
Cost is absent because most price sheets remain under NDA. As a rule of thumb, software-first options such as QuSecure and Keyfactor land on the lower end, while physics-heavy gear like ID Quantique commands premium budgets.
Match solutions to your pain points: protect blockchain assets with Project Eleven, secure nationwide fibre with ID Quantique, and place the rest according to your integration and performance needs.