Imagine your organization gets a clean bill of health from its last external scan—yet within hours, a generative AI-powered attack script exploits an overlooked misconfiguration that was exposed only minutes ago. Attacks are now executed faster and with greater efficiency and scale, meaning security teams can no longer afford periodic visibility. It’s time to evolve from snapshot-based scanning to continuous threat exposure management (CTEM)—a framework designed for this AI-driven era.
Reality of AI-Enhanced Threats
Per Anthropic’s recent Threat Intelligence Report, AI has not only ‘lowered the barriers to sophisticated cybercrime,’ but cybercriminals are now leveraging AI throughout the entirety of their operations.
Generative AI, for example, allows threat actors to create customized payloads and discover misconfigurations in real-time. In 2023, the CL0P Ransomware exploited a zero-day in MOVEit using automated scanning tools. The reality is that most high-severity incidents don’t stem from new vulnerabilities, but from unaddressed or misconfigured controls that slip through traditional security processes. The time between exposure and exploitation is shrinking and CTEM is designed to meet that moment.
What CTEM Really Brings to the Table
CTEM flips the model from static, quarterly scans to ongoing monitoring of exposures. Organizations need a platform that emphasizes exposure and includes misconfigurations, control gaps, policy drift — not just CVEs.
There are a few factors that set the CTEM framework apart from other preventative measures. CTEM prioritizes issues based on operational impact, which exposes business risks. It provides immediate validation testing, real exploitability, and reduces noise. And its continuous remediation enables instant, automated response to any emerging risks.
With the increased risk of AI threats, it’s a no-brainer why they’re a good match for early detection. CTEM platforms use AI and machine learning to analyze security signals across data sources, predicting likely attack paths before they’re used. It leverages control-layer enforcement powered by AI to immediately mitigate validated exposures — even while the full investigation is still unfolding. CTEM allows defenders to see what attackers would exploit and take action before a breach happens.
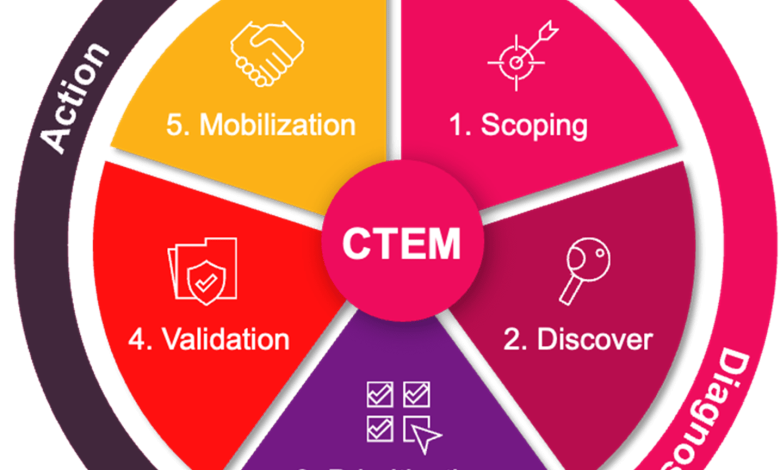
The CTEM Playbook: Five Steps to Staying Ahead
- Gain Unified Visibility
AI-driven attacks thrive in blind spots, where fragmented monitoring creates opportunities for exploitation. By consolidating cloud, on-prem, and hybrid assets into a single view that also integrates data from EDR, firewalls, IAM, and workloads, you’ve given a baseline of truth that enables proactive security. Visibility isn’t just about detection — it’s about eliminating the unknowns that attackers leverage first. - Identify and Validate Exposure
CTEM uncovers misconfigurations, shadow IT, and control drift — and then validates which risks are truly exploitable in the real world. This helps security leaders separate “nice to know” findings from actual priorities. By simulating attacker behavior, CTEM provides proof of exploitability, reducing alert fatigue and sharpening team focus. - Contextualize and Prioritize
Not all risks are created equal. CTEM ranks exposure in business context — factoring in likelihood, blast radius, and potential impact on critical assets. Instead of treating every alert the same, CTEM ensures teams spend their time on the weaknesses that attackers are most likely to weaponize. This approach accelerates remediation while minimizing wasted effort. - Enforce Preemptively
The old model of waiting for a human-in-the-loop response is simply not going to cut it against AI-driven threats. CTEM integrates directly with controls to automatically shut down exploitable attack paths across firewalls, proxies, and identity systems. Enforcement is applied consistently, reducing downtime time and giving security teams confidence that the basics are always covered. - Learn and Improve
Exposure management is an ongoing cycle, not a one-time project. CTEM continuously tests defenses, feeding real-world lessons back into the program. Over time, this moves teams from reactive firefighting toward strategic, long-term resilience. Each cycle strengthens the organization’s ability to anticipate rather than just respond.
Future-Proofing Your Security Posture
In today’s environment, where AI-driven attacks evolve in real time, speed and precision are everything. CTEM provides both by aligning visibility, validation, prioritization, enforcement, and continuous learning into a repeatable framework. Organizations that embrace CTEM are not only defending against current threats but also building a future-ready posture that adapts as attackers do. By shifting from static defense to dynamic, continuous exposure management, security leaders can transform risk into a competitive advantage — staying one step ahead in a landscape where downtime can be the culprit of an organization’s downfall.




