30,458. These are the cyber threat incidents that have been reported so far this year, according to Verizon’s 2024 Data Breach Investigation Report. And we have five months remaining in the year too. These numbers are concerning, and what’s more alarming is the pace at which these cyber-attacks are growing.
After the advent of AI, while all the major industries have evolved and continue to do so, cybercriminals are also developing advanced tools and strategies. Changing your systems’ passwords and updating third-party contracts more often is no longer a reliable solution. The time calls for both individuals and organizations to implement robust cyber-security measures to protect their data and business assets.
If you are worried about your digital business or assets, say no more. This article discusses the most pertinent types of cyber-attacks and provides a solid cybersecurity plan for you to implement in your business.
Cyber Attacks and Why You Should Care About It
With advancements in technology, malicious actors also develop more advanced tools and strategies. The increasing dangers highlight the immediate requirement for strong security measures to protect our online domain. Research from the National University suggests there has been a 75% rise in the Malware-free activity detected identity attacks in 2023. And these numbers are only prone to increase.
The threat of cyber-attacks is also progressing in parallel to businesses and organizations aimed at countering them. An immediate effect of this is the surge in claims for cybersecurity professionals a situation that continues to prevail in today’s growing tech-focused systems. Organizations look for qualified candidates with professional training such as a bachelor in cybersecurity program in developing and implementing their business’ cybersecurity policies. These programs are the primary basis for cultivating great comprehension of the different aspects of cybersecurity.These programs equip them to handle the ever rising incidences of threats in the world today that being in the digital front.
Malware Attacks
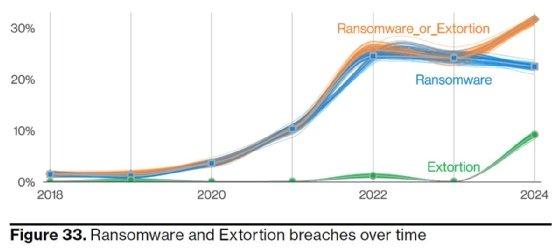
Probably the biggest type of cyber-threat, Malware covers almost all Threat actors who employ malware attacks to illicitly access systems and make them non-operational, causing damage, pilfering confidential data, and possibly erasing essential operating system files. According to a report by the IBM Security X-Force Threat Intelligence Index 2024, ransomware makes up a total of 30% of all cyberattacks reported in 2024.
Increase in Ransomware Attacks
Ransomware attacks are growing more intricate, affecting companies of every size. There are hundreds of examples of notable companies worldwide that fell victim to these ransomware attacks in the last few years.
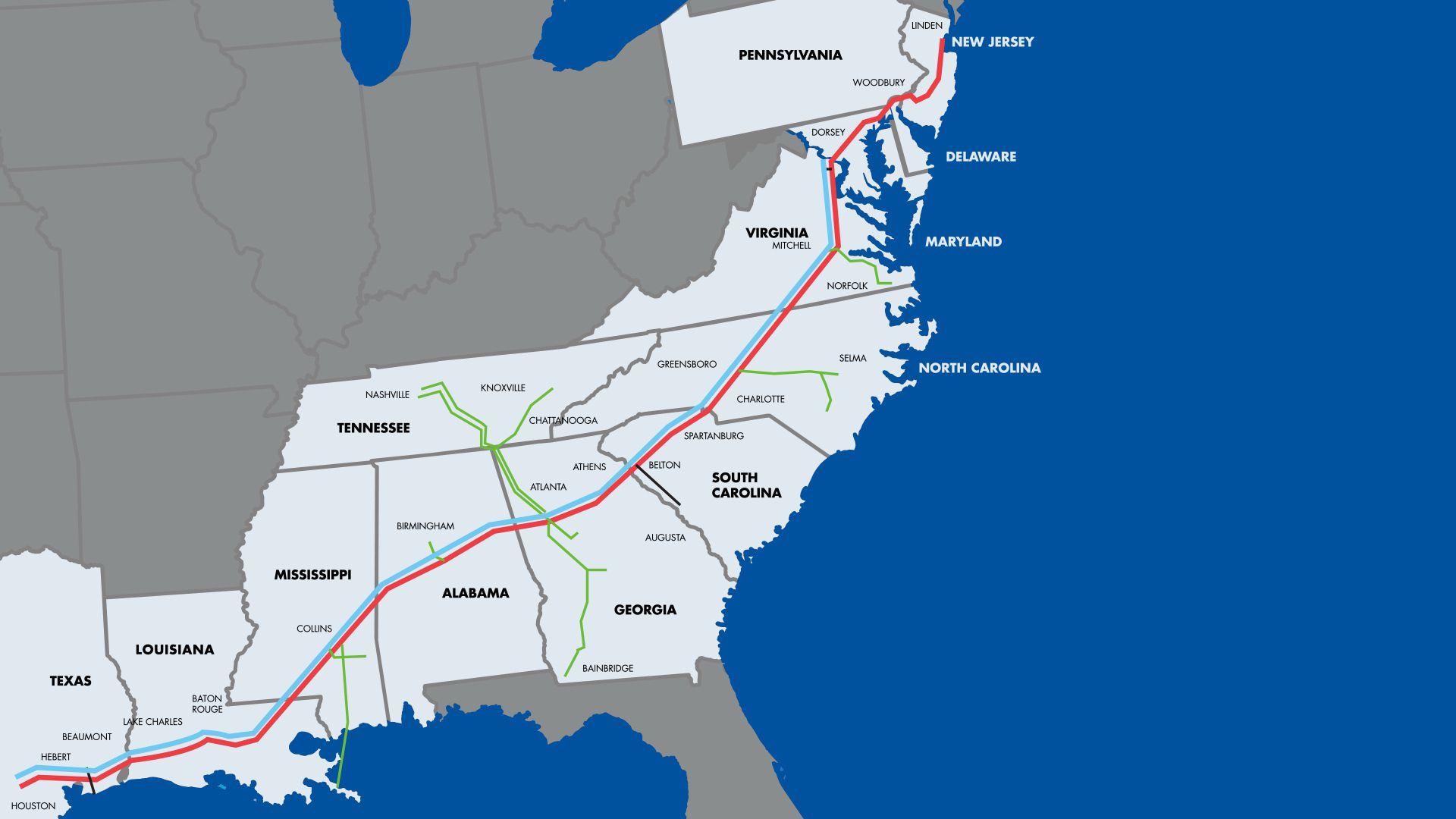
The Colonial Pipeline breach illustrated the increasing complexity of ransomware. It led to extensive chaos and significant economic damage. This underscores the vital need for establishing robust backup systems to safeguard against such risks.
The Colonial Pipeline system. Image: courtesy of Colonial Pipeline
Phishing Attacks
Phishing attacks trick individuals into revealing confidential information using social manipulation. How often do you get an email from a Nigerian prince who wants to escape a war state and wants to transfer his millions into your bank account? That’s just one example.
How to Ensure Your Business Stays Safe from Cyber Threats in 2024
- Use the Power of Artificial Intelligence
Artificial intelligence is like a double-edged sword. This powerful technology offers both opportunities and challenges in cybersecurity. To utilize the power of AI against cyber threats, businesses can adopt the following five lines of effort.
- Assure AI Systems: Businesses should promote secure-by-design AI software adoption among diverse stakeholders. They must also develop best practices and guidance for robust AI development and implementation.
- Protect Critical Infrastructure from Harmful AI Use: You should identify and mitigate AI threats to safeguard vital infrastructure. Must collaborate with government agencies and industry partners to enhance AI security measures.
- Collaborate and Communicate on Key AI Efforts: Decision-makers should engage in interagency and international collaboration to shape AI policy and advance global security standards. This fosters transparency and cooperation in AI-based software initiatives.
- Expand AI Expertise in Our Workforce: Companies should educate and recruit talent proficient in AI systems and techniques. They must also ensure staff’s comprehensive understanding of AI-based software’s legal, ethical, and technical aspects.
- A Formal & Well Documented Cybersecurity Program
- Data Governance and Classification: Businesses can implement policies and procedures for data handling and classification. This will ensure sensitive information is protected correctly according to confidentiality.
- Access Controls and Identity Management: Adequate access management can help control management processes by managing user access to systems and data. This will reduce the risk of unauthorized access as companies can give limited access to only those who require it for their job roles.
- Configuration Management: Review and update system configurations regularly to ensure they align with security best practices. Proper configuration management also helps prevent vulnerabilities and unauthorized changes to system settings.
- Prudent Annual Risk Assessments
- Identify and Document Risk: Identify potential risks to your information systems. Document each risk by noting how it might affect your business. This will help you identify, understand, and mitigate potential threats.
- Evaluate and Categorize Risks: Assess the impact and likelihood of each identified risk. Categorize them based on their potential effects on confidentiality, integrity, and data availability. This step helps in setting up appropriate controls.
- Update Controls Regularly: The revision of security controls addresses technological changes and emerging threats. Regular updates ensure that your defenses remain effective against new types of cyberattacks.
- Review and Adapt: Regularly update your risk assessment process to keep it current. Consider changes in your information systems, nonpublic information, and business operations to maintain a robust cybersecurity posture.
- A Reliable Annual Third-Party Audit of Security Controls
This might not be a cost-effective solution for small businesses, but it comes with a set of benefits. An independent auditor allows you to assess your security controls.
- Compliance with Standards: This allows you to ensure the audit is conducted according to recognized standards. Compliance with these standards ensures that your security measures meet industry benchmarks.
- Address Identified Weaknesses: Identify and correct any weaknesses during the audit. A clear plan for addressing vulnerabilities is vital to improving your security posture.
- Ongoing Monitoring and Updates: Update your security measures regularly based on audit findings. Yet continuous monitoring and improvement are vital in staying ahead of new threats.
Wrapping Up
Stating that cybersecurity is the need of the hour is not an exaggeration at all. Form the above research it is clear that theses cyber security measures should be implemented irrespective of the size of the business or its geographical location on the earth’s map. Big int’l tech companies are dedicating a lot of money towards building structures and systems for their organisations that effectively cannot be penetrated by cyber-criminals especially with the arrival of AI. There are ways and ways of doing things; one can acquire the right certification and knowledge to be ahead of the game.