Here is a current picture of cybersecurity landscape: it has become a boardroom priority for businesses of all sizes. Of course, it is a welcome change. This widespread transformation has happened because of one simple reason. Small, mid-sized and even enterprise organizations now realize that a single breach can cause grave financial losses as well as reputational damage to the brands.
Moreover, there is an increasing awareness among IT security leaders that deploying firewalls, antivirus software and intrusion detection systems does match the capabilities of a cyber attacker today. Therefore, assuming you’re secure can be dangerous. That’s where Vulnerability Assessment steps in.
A structured, highly important and first line of defence, vulnerability assessment process includes identifying, analysing and prioritizing weaknesses across the IT environment. This changes the game because you are finding the loopholes and plugging them before an attacker exploits them.
This blog shows you why vulnerability assessments are a critical investment while offering a step-by-step checklist you can apply to your organization.
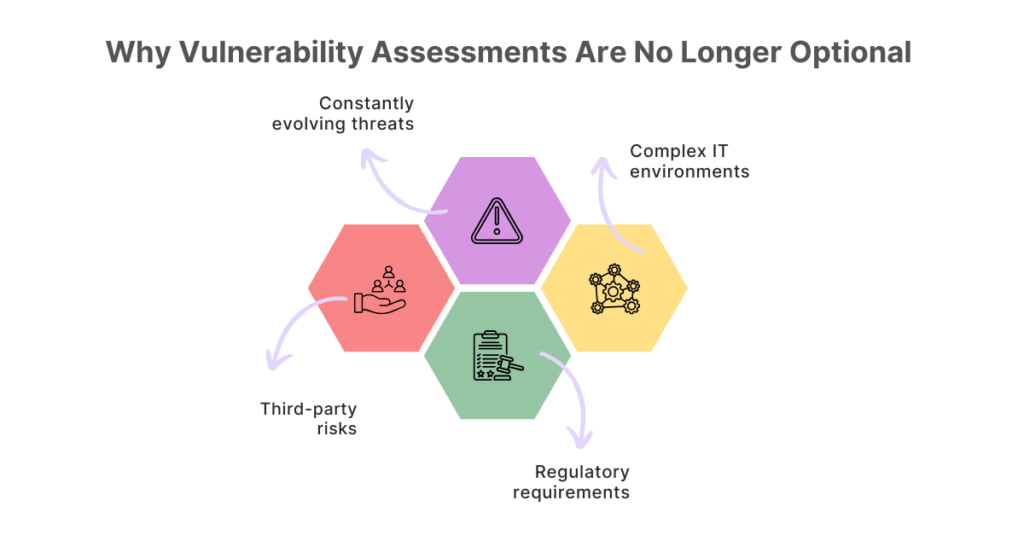
Why Vulnerability Assessments Are No Longer Optional
Snap back to 2010. A software update and a solid firewall were enough to give businesses confidence in their security posture. Now fast forward to the new, digitized era of cloud adoption, mobile-centric systems, IoT-device driven world of 2025. And what? That confidence is certainly misplaced, you’d agree.
Here are some specific reasons why we think businesses can’t ignore this practice anymore, which essentially acts as the first line of defence:
- Constantly evolving threats: New vulnerabilities emerge daily. A missed patch could mean exposure to ransomware or data theft.
- Complex IT environments: From SaaS platforms to hybrid cloud infrastructures, the attack surface has multiplied.
- Regulatory requirements: Frameworks like GDPR, HIPAA, and PCI DSS mandate continuous security assessment and vulnerability scanning.
- Third-party risks: Vendors and partners often extend your attack surface in ways you can’t fully control.
What Is a Vulnerability Assessment?
Vulnerability Assessment can be understood as the basics of cybersecurity program. That means the first thing perhaps in the long list of security strategy pointers. As to the process, it involves systematically reviewing your systems, networks and applications. The objective is to uncover weak points that could be exploited.
Unlike pentesting, which simulates real world attacks, a vulnerability assessment focuses more on breadth than depth. It basically helps organizations to gain visibility into all their exposures.
Key components usually include:
- Automated scanning tools to detect known vulnerabilities.
- Configuration reviews to identify insecure settings.
- Patch management checks to highlight outdated systems.
- Risk scoring helps prioritize remediation efforts.
The ultimate goal? To ensure that IT asset flaws are found and fixed by internal security teams before malicious actors could exploit them externally.
Vulnerability Assessment vs. Security Assessment
Both terms have being used by experts, journalists and researchers interchangeably sometimes. However, they are different.
A Vulnerability Assessment is narrower, focused on identifying specific flaws like missing patches or weak configurations. A Security Assessment, on the other hand, is broader. It evaluates policies, employee behaviour and overall governance in addition to technical weaknesses.
It is important to understand the distinction because wrong cybersecurity decisions based on wrong business context can prove to be costly.
The Business Value of Vulnerability Assessments
Some businesses are reluctant to understand and accept the value vulnerability assessments bring to the table. But it definitely goes beyond IT. The outcomes of a vulnerability assessment help in business continuity, meet compliance objectives and retain customer trust. Here are some other benefits:
- Cost savings: Fixing vulnerabilities early is far less expensive than remediating after a breach.
- Regulatory alignment: Most compliance audits require documented security assessment results.
- Improved customer trust: Clients are more likely to work with businesses that demonstrate proactive cyber hygiene.
- Stronger resilience: Regular assessments reduce downtime and operational disruptions.
Need a real-world example? Consider the case of Equifax, which lost over $4 billion in value after a data breach that stemmed from a missed patch. A simple, timely vulnerability assessment could have prevented it.
The Ultimate Vulnerability Assessment Checklist
Here’s a practical checklist businesses can use as a guide:
- Define the Scope
- Identify critical systems, applications, and data.
- Include cloud services, endpoints, and third-party integrations.
- Gather an Asset Inventory
- List all servers, devices, software, and network components.
- Don’t overlook shadow IT—unauthorized tools employees may be using.
- Run Automated Vulnerability Scans
- Use reputable scanning tools to detect known vulnerabilities.
- Schedule scans regularly (weekly, monthly, or quarterly based on risk level).
- Analyze and Prioritize Risks
- Assign severity ratings (low, medium, high, critical).
- Focus on vulnerabilities with the highest likelihood of exploitation.
- Validate with Manual Reviews
- Automated scans may miss misconfigurations or business logic flaws.
- Manual validation helps eliminate false positives.
- Patch and Remediate
- Apply security patches promptly.
- Reconfigure weak settings and remove unnecessary access.
- Re-test After Fixes
- Confirm that remediation efforts were successful.
- Document changes for compliance records.
- Report and Educate
- Share results with leadership to secure buy-in for further investments.
- Train employees on secure practices to reduce recurring issues.
How Vulnerability Assessments Fit Into a Larger Cybersecurity Strategy
As pinpointed before, vulnerability assessment is the foundation. Or you should see it as a building block in a broader cybersecurity strategy. Here’s how it fits:
- With penetration testing: Once vulnerabilities are identified, penetration testing digs deeper into how they could be exploited in real-world scenarios.
- With incident response planning: Knowing your weak points helps design faster containment strategies.
- With ongoing monitoring: Continuous monitoring ensures that vulnerabilities don’t re-emerge after patches.
How to Get Started with Vulnerability Assessment
The first step is to acknowledge and accept that security is important, integral and key aspect for business building, growing and embracing transformation. Starting with a clear Vulnerability Assessment provides a baseline of your current risk posture and a roadmap for improvement.
If you’re considering a structured approach, you can explore professional Vulnerability Assessment services that provide in-depth expertise and advanced tools tailored to business needs. And if you want to understand broader cybersecurity strategies, you can always learn more through trusted providers like CyberNX.
Conclusion
Cybersecurity isn’t a trend but a vital practice in the larger scheme of things. Think of vulnerability assessment as the exercise that consistently identifies, tests and reinforces weak spots before attackers find them.
A Vulnerability Assessment isn’t just a technical checkbox; it’s a critical component of protecting your revenue, your reputation, and your future.
In a world where breaches can cost millions and erode years of trust overnight, exposing weak points before hackers strike could very well be the smartest business move you make this year.