Abstract: The article presents a system analysis of modern approaches to ensuring the security of applications developed on the Java platform. The purpose of the study is to classify current threats and form a set of practical recommendations for their neutralization at all stages of the software life cycle. The work considers common attack vectors systematized in the OWASP Top 10 project, analyzes the built-in security mechanisms of the Java platform, such as Security Manager and Java Cryptography Architecture, and describes secure coding practices. The results of the study are summarized in the form of a multi-level security model integrating static and dynamic code analysis. The practical significance of the work lies in the possibility of using the proposed methods by development engineers and security specialists to build secure corporate systems and reduce the risks associated with cyberattacks.
Keywords: application security, Java, OWASP Top 10, secure development, static code analysis, SAST, dynamic analysis, DAST, DevSecOps, SQL injection.
The Java platform holds a leading position in the enterprise development segment due to its performance, cross-platform functionality, and well-developed ecosystem. At the same time, the widespread use of Java applications makes them a priority target for cyber attacks. The increasing complexity of software systems and the constant emergence of new attack vectors determine the high urgency of the problem of ensuring their security. Information protection has ceased to be a task solved exclusively at the network infrastructure level, and has shifted directly to the application code level. Insufficient attention to safe development practices leads to financial and reputational losses for businesses.
The purpose of this article is to analyze and systematize the best practices for protecting Java applications from modern threats, as well as to form an integrated approach to integrating security into the development process.
The landscape of modern threats: OWASP classification
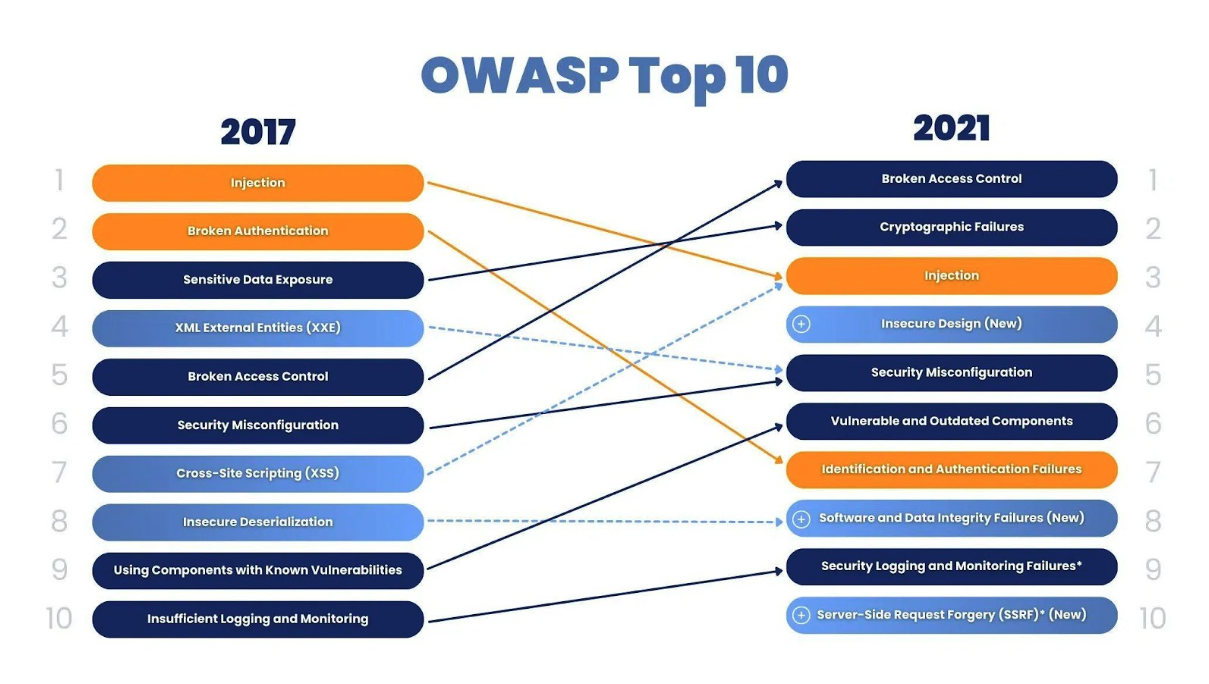
To systematize web application security threats, the Open Web Application Security Project (OWASP) has been widely recognized, which regularly publishes a list of the ten most critical security risks [3]. This document serves as a fundamental guide for developers and security professionals around the world. The most common vulnerabilities relevant to Java applications include:
- Injections: The injection of malicious code, most often SQL code, into database queries. This may lead to unauthorized access, modification, or deletion of data.
- Broken Authentication: Vulnerabilities in session management and authentication mechanisms that allow attackers to compromise user accounts.
- Cross-Site scripting (XSS): The introduction of malicious scripts on web pages, which are then executed in the user’s browser, which allows sessions to be stolen or redirected to phishing sites.
- Insecure Deserialization: A vulnerability that occurs when processing serialized objects from untrusted sources, which can lead to remote code execution.
Using components with known vulnerabilities: Using third-party libraries and frameworks containing publicly known vulnerabilities, which is one of the most frequent attack vectors.
Understanding these attack vectors is the starting point for building an effective defense strategy.
Built-in Java platform protection mechanisms
The Java platform was originally designed with security requirements in mind and includes a number of built-in mechanisms for creating secure applications. One of these components is the Security Manager, which allows you to execute code in the so-called “sandbox”, limiting its access to system resources such as the file system or network connections. By defining a strict security policy, the potential damage from the execution of compromised code can be significantly reduced [1].
Another important element is the Java Cryptography Architecture (JCA). It provides developers with a unified API for performing cryptographic operations, including encryption, digital signature management, and hash sum generation. The use of JCA makes it possible to implement reliable data encryption during storage and transmission, which is a mandatory requirement for many systems [4]. These built-in tools create a solid foundation on which additional layers of protection should be built.
Secure Coding and Dependency Management Practices
To protect the code in practice, it is necessary to apply specific methods. Against SQL injections, parameterized queries (Prepared Statements) are used, which treat user input as data rather than as executable code. To prevent XSS attacks, all user input must undergo strict validation and cleaning before being displayed in order to neutralize malicious scripts. In addition, the security of third-party dependencies is ensured by automatic scanning for known vulnerabilities using tools integrated into build systems [3].
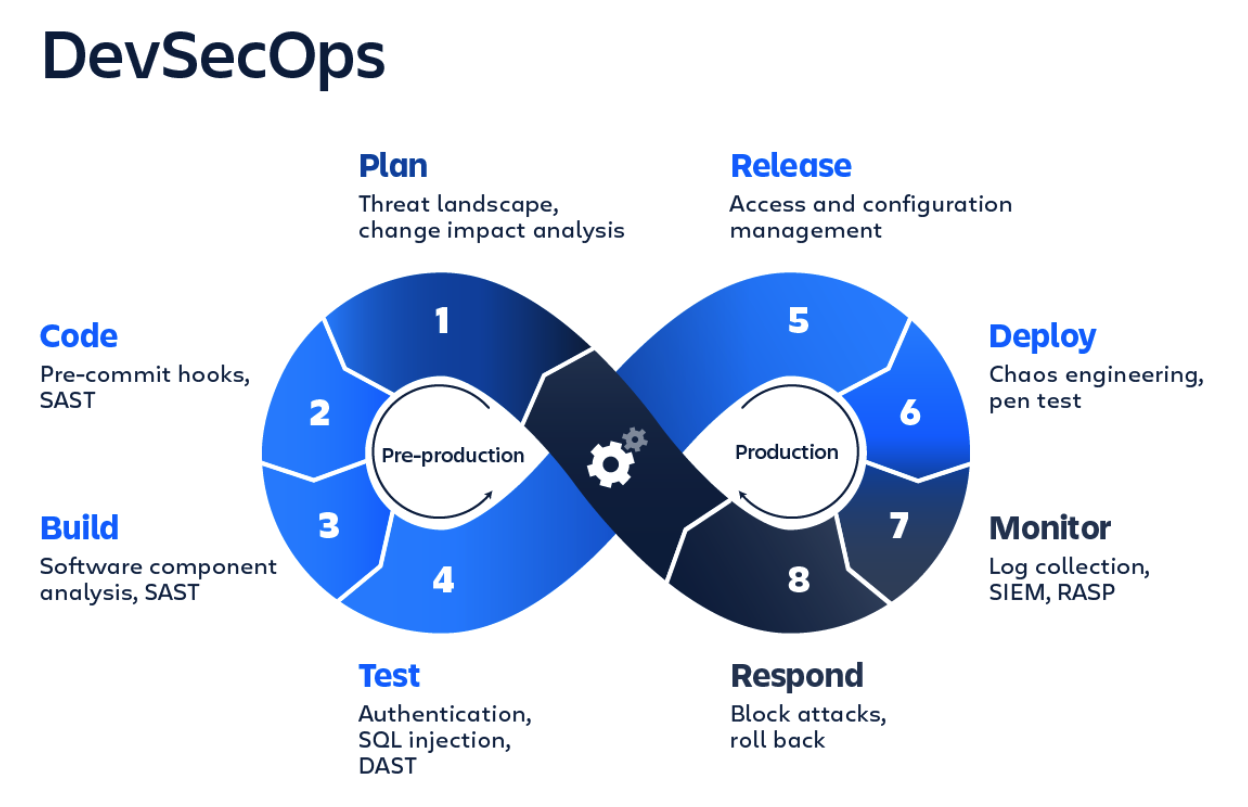
Integration of security into the development lifecycle (DevSecOps)
The modern approach to development involves the integration of security practices at all stages of the product lifecycle, which is called DevSecOps. This approach is based on the use of automated tools for continuous security analysis.
Static Application Security Analysis (SAST) is an analysis of the source code for potential vulnerabilities without running it. SAST tools such as SonarQube or Checkmarx integrate into the CI/CD pipeline and allow you to identify problems early in development. They are effective for detecting SQL injections, incorrect error handling and other code defects [2].
Dynamic Application Security Analysis (DAST), in turn, tests an already running application, simulating malicious attacks. DAST tools, such as OWASP ZAP, help identify vulnerabilities that appear only at runtime, such as incorrect server configuration or errors in session management. The combined use of SAST and DAST provides comprehensive control over the security status of the application.
Effective protection of Java applications is a continuous and multi-level process. It requires a combination of built-in platform mechanisms, secure coding, and dependency management. The key element is the integration of automated analysis tools (SAST and DAST) into the CI/CD pipeline, which allows early identification and elimination of vulnerabilities systematized in the OWASP Top 10, thereby minimizing risks and costs.
List of literature
- Schildt H. Java: A Complete Reference, 11th edition. – New York : McGraw-Hill Education, 2018. – 1248 p.
- Kim, G. The Phoenix Project: a novel about IT, DevOps and how to help your business win / G. Kim, K. Behr, G. Spafford. – Portland, OR : IT Revolution Press, 2014. – 376 p.
- OWASP Top 10:2021. The ten most serious threats to web application security [Electronic resource] // OWASP Foundation. – 2021. – URL: https://owasp.org/www-project-top-ten /.
- Viega, J. Creating secure software: how to avoid security problems correctly / J. Viega, J. McGraw. – Boston, MA : Addison-Wesley Professional, 2001. – 493 p.