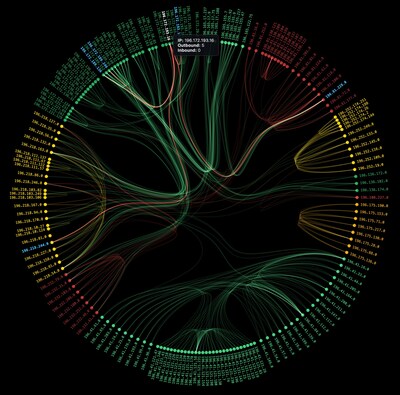
Cybersecurity leader expands its data foundation with 1T+ internet traffic flows to deliver deeper third-party risk insights and stronger cyber ratings
BOSTON, Jan. 29, 2026 /PRNewswire/ — Black Kite, the leader in third-party cyber risk management, today announced the release of ThreatTrace™, its new capability that improves threat detection using NetFlow and DNS telemetry to strengthen an organization’s visibility into third-party cyber risk. Black Kite is the first TPCRM vendor to incorporate this deep level of visibility into third-party cyber risk monitoring and ratings, enabling teams to proactively take targeted action with their vendors.
“The release of ThreatTrace™ reflects our continued commitment to building the most comprehensive and trusted data foundation for third-party risk intelligence,” said Candan Bolukbas, CTO & Founder, Black Kite. “Internet traffic flows provide powerful signals of potential compromise. When an organization’s digital assets repeatedly connect to known malicious infrastructure, high-risk regions, or unusual services, it’s a strong indicator that something may be wrong – and teams need to act quickly.”
NetFlow and DNS telemetry have long been valuable data sources in the SecOps world for detecting suspicious activity and deepening cyber investigations. With the release of ThreatTrace™, risk teams can detect new IOCs and anomalies to act faster and stay ahead of third-party threats through:
- Stronger cyber intelligence with a new set of controls added under the IP Reputation risk category, informed by NetFlow and DNS telemetry
- Broader IOC and anomaly detection, including botnet-related activity, reconnaissance/C2 communication, potential data exfiltration, and more
- Greater supply chain visibility by uncovering new subdomains and connected third-party service providers.
With ThreatTrace™, TPRM teams can now proactively detect new IOCs and anomalies, including:
- Botnet Infection: Identifies IP addresses that have been blacklisted by multiple threat intelligence sources, indicating that an internal asset, like a server, IoT device, or workstation, is likely compromised and actively participating in malicious activity, such as spamming, DDoS attacks, or C2 operations.
- Suspicious Outbound Activity: Detects active compromises by correlating DNS queries to high-risk domains (e.g., Tor sites, hacker forums, or C2 servers) with corresponding network traffic from the company’s IPs.
- Active Threat Actor Targeting: Detects when known malicious IP addresses, such as botnets or C2 servers, are actively interacting with a company’s digital assets, indicating an organization is being targeted for reconnaissance or attack.
- Traffic Baseline Deviation: Flags significant deviations from established traffic patterns, including unusual data volume spikes, connections to previously unseen high-risk IPs, and the use of abnormal ports, which are potential markers of data exfiltration.
- Geopolitical and Service Risks: Identifies unauthorized services and suspicious data flows directed toward high-risk or sanctioned countries to detect both potential data leakage and compliance violations.
ThreatTrace™ leverages NetFlow and DNS telemetry to strengthen cyber intelligence, helping teams detect threats earlier and stay ahead of third-party cyber risk. To learn more, visit https://blackkite.com/solution-briefs/black-kite-threattrace.
About Black Kite
Black Kite is the AI-native third-party cyber risk management platform trusted by over 3,000 customers to manage every supplier and every risk across their extended ecosystem. Powered by the industry’s highest-quality risk intelligence, spanning over 40 million companies, Black Kite is differentiated by the accuracy, transparency, and actionability of its data. The platform automates vendor monitoring and risk assessments, surfacing reliable insights into ransomware susceptibility, regulatory gaps, financial exposure, and more. With Black Kite, security and risk teams gain always-on visibility and trusted intelligence to act early, reduce exposure, and stay ahead of third-party threats. Black Kite has received numerous industry awards and recognition from customers. Learn more at www.blackkite.com, or on the Black Kite blog.
Media Contact:
Michelle Kearney
Hi-Touch PR
443-857-9468
[email protected]
View original content to download multimedia:https://www.prnewswire.com/news-releases/black-kite-introduces-threattrace-to-detect-new-indicators-of-compromise-iocs-using-internet-traffic-flow-302672732.html
SOURCE Black Kite