Security teams face a straightforward challenge every day: they must determine whether an incoming connection, email sender, or domain is safe to trust. An IP reputation check is a quick way to see if an address has a history of malicious activity, and the same idea applies to domain reputation. These two signals often decide whether a system should block, challenge, or allow traffic.
In my experience working with threat analysts, the biggest challenge isn’t running the check; it’s knowing what the results actually mean. A score alone doesn’t tell the whole story. You need context: where the IP is located, how it behaved over time, whether the domain has suspicious DNS changes, or if the address is tied to malware distribution.
This guide explains how IP and domain reputation checks work, what data is relevant, and how to utilize them as part of a comprehensive cyber intelligence workflow. The goal is to make the process simple, practical, and repeatable, whether you’re analyzing a login anomaly or investigating a phishing attempt.
Before we look at tools and techniques, here’s what an IP reputation check actually tells you and how it fits into real-world threat detection.
What an IP Reputation Check Actually Tells You
An IP reputation check gives you a snapshot of how an address has behaved across the internet. It shows whether an IP is associated with suspicious activity, risky networks, or known threat sources. Analysts use this to decide if traffic should be blocked, challenged, or monitored more closely.
In my experience, the most useful checks combine historical behavior with technical attributes. A high-risk score usually reflects a pattern, not a single event. For example, repeated login abuse, spam activity, or contact with malware services. A low score doesn’t guarantee safety either, especially when the IP is part of a shared or dynamic network.
Here are the common signals included in a reputation check:
Key Data Returned in an IP Reputation Check
- Risk Score: A numeric value showing how likely the IP is to be malicious.
- Threat Flags: Indicators like bot activity, brute-force attempts, spam, C2 communication, or malware hosting.
- Network Type: Whether the IP belongs to a proxy, VPN, TOR exit node, hosting server, or residential network.
- Geolocation & ASN: Location and the Autonomous System that owns the address, useful for spotting inconsistent login patterns.
- Blacklist Presence: Whether the IP appears on spam or abuse blocklists.
- Historical Behavior: Past abuse reports, unusual traffic bursts, or repeated failed authentications.
- Reverse DNS & Hostname Clues: Domains tied to known malicious infrastructure or throwaway servers.
Quick Interpretation Table
| Signal | What It Indicates |
| Appears on DNSBL/RBL lists | Spam, bot, or compromised system |
| Hosted on VPN/TOR | Potential anonymity or evasion |
| ASN tied to cloud hosting | Higher risk for scripted or automated attacks |
| Sudden geolocation shifts | Credential stuffing or account takeover |
| Long history of abuse | Strong indicator of active malicious behavior |
These signals help you understand whether an IP should be trusted, not just at a single moment, but based on thousands of behaviors that came before it.
Domain Reputation vs. IP Reputation: Why Both Matter for Cyber Intelligence
IP reputation checks are a strong first filter, but they only reveal half the picture. Domain reputation indicates whether a domain has been used for phishing, malware distribution, or other deceptive activity, and often reveals threats that a simple IP lookup can’t.
From my experience reviewing phishing cases, attackers frequently rotate IP addresses but keep the same domain or DNS pattern. A “clean” IP may hide a domain that was hosting phishing pages yesterday or redirecting traffic through compromised servers.
Why Security Analysts Consider Both
- Domains move across IPs, but their malicious intent usually stays the same.
- IP addresses may be shared, especially on hosting services; domains provide a more stable signal.
- DNS history reveals hidden infrastructure changes that attackers try to hide.
- Phishing campaigns often recycle domains, even when switching networks.
When combined, domain and IP checks offer a clearer, more reliable view of the threat landscape, which is why cyber intelligence teams treat them as complementary signals instead of interchangeable tools.
How DNS Records Impact Domain Reputation
DNS records are often the strongest clue that something is wrong with a domain. Changes in A, MX, NS, or TXT records can reveal malicious behavior long before the domain appears on blocklists.
Analysts look at DNS patterns to see how stable or suspicious a domain is. For example, phishing domains often rotate IP addresses rapidly or switch to new name servers in short bursts. In my investigations, sudden record changes within hours or days usually point to an active campaign or infrastructure rebuild.
Here’s how DNS records impact reputation:
Critical DNS Factors
- Record Volatility: Frequent IP changes may indicate fast-flux hosting or evasion tactics.
- NS Record Changes: Switching name servers multiple times suggests instability or domain hijacking.
- MX Records: Misconfigured or suspicious mail servers often align with spam/phishing behavior.
- TXT Records: Missing SPF, DMARC, or DKIM settings lower email trustworthiness.
For deeper investigation, security teams often review DNS record history using tools like whoisfreaks.com to detect long-term patterns that attackers try to hide.
A stable DNS footprint usually signals legitimacy; erratic patterns usually mean the opposite.
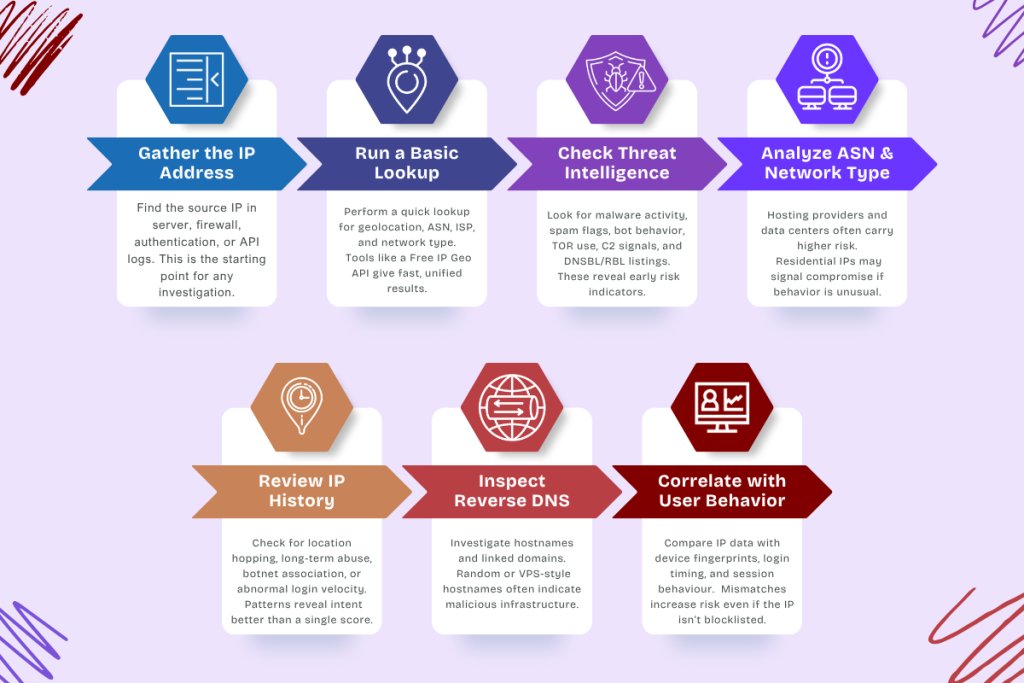
How to Run an IP Reputation Check (Step-by-Step)
Running an IP reputation check is straightforward, but interpreting the results is where experience matters. Here’s a step-by-step process that security teams use when investigating suspicious logins, payment attempts, or network traffic anomalies.
From my experience working with SIEM and SOC workflows, the key is to combine multiple signals instead of relying on a single score.
Step-by-Step Process
1. Gather the IP address from logs
Start with the source IP. This usually comes from authentication logs, firewall logs, server access logs, or API telemetry.
2. Run a basic lookup
Perform a standard lookup to retrieve geolocation, ASN, network type, and hostname.
For geolocation, many teams use a Free IP Geo API like ipgeolocation.io because it returns location, time zone data, network type, and risk indicators in one response.
3. Check threat intelligence sources
Look for:
- Malware flags
- Spam activity
- Bot behavior
- C2 communication
- TOR or proxy usage
- Known attack patterns
If the IP appears on DNSBL or RBL lists, it’s a strong early signal.
4. Analyze the ASN and network type
Hosting providers and data centers are riskier because attackers automate traffic through them.
Residential IPs aren’t always clean either, but sudden behavior spikes can mean compromise.
5. Review the IP’s history
Check if:
- It has switched locations frequently.
- It has a long abuse trail.
- It belongs to a botnet or a compromised network.
- It shows abnormal login velocity.
History often reveals intent better than a single score.
6. Check reverse DNS and associated domains
A suspicious hostname (for example, a string of random characters or disposable VPS naming patterns) can reveal malicious infrastructure.
7. Correlate results with user behavior
After gathering technical data, compare it with:
- Device fingerprints
- Login timing
- Session behavior
- Past activity
In my experience, mismatched patterns (new device + new IP + new location) are worth escalating even if the IP is not yet flagged on blocklists.
This workflow helps you confirm whether the IP is simply unusual or actively malicious.
Key Signals That Indicate a High-Risk IP or Domain
High-risk indicators are patterns that consistently appear in malicious traffic. Analysts rely on these signals because they’re difficult for attackers to hide, even when they rotate IPs or switch domains.
Here are the signals that most often reveal a threat.
Common High-Risk Indicators
- TOR or VPN usage
Often linked to anonymity or evasion during attacks. - Hosting provider or cloud network IPs
Attackers automate scripts and bots from VPS services. - Fast-flux DNS patterns
Rapid rotation of IPs to avoid takedowns. - Reputation score above risk threshold
Indicates repeated abuse or a history of malicious behavior. - Associated malware or phishing reports
Shows the IP or domain is part of a known campaign. - Unusual geolocation patterns
For example, a user account normally in Berlin suddenly logs in from Brazil, then Hong Kong. - Open ports suggesting botnet activity
Ports used for remote control, including 23, 2323, 8080, and 5000. - Disposable or newly registered domains
Attackers frequently use domains less than 30 days old.
In my investigations, the strongest signal is a combination of mismatched behavior, such as a new device, a new location, and an IP with a sketchy history. Attackers rarely get all details consistent, and that’s where these indicators help.
Tools and APIs Commonly Used for IP and Domain Reputation Checks
Different teams use different tools, but the goal is always the same: gather enough context to decide whether the traffic is safe. In my experience, no single tool gives a complete picture. Analysts usually combine several sources to reduce blind spots.
Most tools fall into three categories:
1. IP and Domain Intelligence APIs
These services return raw data that you can integrate directly into your applications, firewalls, or SIEM systems. They typically provide:
- Risk scores
- Threat flags
- ASN and network type
- Geolocation
- Domain age
- DNS snapshots
APIs are popular because they help automate detection instead of relying on manual checks.
2. OSINT and Reputation Databases
Security teams also use public or semi-public sources to cross-check results. These databases reveal whether an IP or domain has been involved in:
- Spam
- Phishing
- Botnet activity
- Malware hosting
- TOR traffic
- Brute-force attempts
These sources help validate whether the initial results are part of a larger pattern.
3. Security Platforms and Monitoring Tools
SIEM, SOAR, and WAF platforms often bundle reputation insights into their dashboards. They correlate IP and domain behavior with:
- User activity
- Endpoint logs
- Application traffic
- Authentication events
This correlation matters. A standalone lookup can flag something as risky, but a security platform shows whether that IP interacted with your environment in a meaningful way.
The important thing isn’t which tool you choose; it’s how you combine the signals they provide. One source may show the IP as clean, while another reveals abuse incidents from last week. Cross-checking prevents false confidence and helps analysts make decisions based on patterns, not isolated data points.
When to Trust Reputation Scores (and When Not To)
Reputation scores look definitive, but they’re only as reliable as the data behind them. I’ve seen clean scores tied to active attacks and high-risk scores triggered by harmless shared networks. Knowing when to trust the rating and when to question it makes a huge difference.
When Scores Are Generally Reliable
Scores tend to be trustworthy when they reflect consistent historical behavior. For example:
- An IP is repeatedly listed for spam.
- A domain linked to malware distribution
- Addresses tied to TOR exit nodes
- VPS-based traffic is hitting login endpoints at odd hours.
These aren’t one-off anomalies. They’re patterns. If a score has been high for weeks or months, there’s usually a good reason.
When Scores Can Mislead You
There are situations where the score doesn’t tell the whole story:
- Dynamic IP pools: A user may inherit an IP that was abused by someone else hours earlier.
- Shared hosting: Hundreds of websites share the same IP. One malicious site can affect all others.
- Brand-new domains: New doesn’t always mean dangerous; many legitimate businesses set up fresh domains.
- Regional networks with noisy traffic: Some providers have naturally higher risk profiles due to volume.
In practice, I treat the score as a starting point. Then I compare it with what I know about the user’s behavior, device, login pattern, and geography. If the score and the behavior don’t match, that’s a sign to dig deeper.
Reputation is useful, but it shouldn’t decide for you. It should guide your investigation, not replace it.
Summary Table: IP Reputation Check at a Glance
| Check Type | Purpose | Key Signals/Indicators | Suggested Tools |
| IP Reputation | Detect malicious IPs, botnets, and suspicious traffic | Risk score, blacklist presence, VPN/TOR usage, ASN, geolocation | ipgeolocation.io (Free IP Geo API), OSINT databases |
| Domain Reputation | Identify phishing or malicious domains | DNS history, A/MX/NS record changes, domain age, and hosting patterns | whoisfreaks.com (DNS record history), reputation APIs |
| Correlation | Combine IP & domain insights | User behavior, login anomalies, endpoint logs | SIEM, WAF, SOAR platforms |
| Actionable Decision | Block, challenge, or monitor traffic | Repeated abuse history, suspicious geolocation, fast-flux DNS | Security workflow tools, automated rules |
This table condenses all the critical information for analysts, developers, and cybersecurity teams at a glance, helping make quick, evidence-based decisions.
Conclusion
IP and domain reputation checks are essential components of modern cyber intelligence. They don’t just tell you whether an IP or domain is “good” or “bad”; they reveal patterns, history, and signals that guide security decisions.
From my experience, the most effective approach combines automated reputation checks with context-aware analysis. Look at the history, examine behavior patterns, cross-check multiple sources, and correlate with your environment. A single score never tells the full story, but together, these signals help reduce risk, detect phishing campaigns, and prevent unauthorized access.
By integrating tools like ipgeolocation.io for geolocation insights and whoisfreaks.com for DNS record history, teams can build a robust, data-driven workflow that strengthens overall cyber intelligence, protecting networks and users more effectively.
Frequently Asked Questions (FAQs):
Q1: What is an IP reputation check?
A: An IP reputation check evaluates an IP address based on its historical behavior and threat indicators. It highlights risks such as spam, bot activity, malware hosting, VPN/TOR usage, and blacklisting. Analysts use these checks to determine whether traffic should be allowed, challenged, or blocked.
Q2: How do you check a domain’s reputation?
A: Domain reputation is assessed by reviewing DNS history, A/MX/NS record changes, domain age, and associated malicious activity. Tools like whoisfreaks.com provide historical DNS records, while reputation APIs aggregate data from threat intelligence sources to flag phishing or malware activity.
Q3: What causes an IP address to have a bad reputation?
A: Bad IP reputation often comes from repeated malicious activity, such as sending spam, hosting malware, participating in botnets, or acting as a proxy for attacks. Even dynamic or shared IPs can inherit a poor reputation if previously abused.
Q4: Is IP reputation important for cybersecurity?
A: Absolutely. IP reputation checks help security teams identify high-risk traffic, prevent unauthorized access, and detect phishing or malware campaigns. Combined with domain checks and behavioral analysis, they form a critical part of proactive cyber defense.